Practical Malware Analysis Chapter 1 Lab 2

Contents
As the first writeup got a little bit long, this one will be a little bit shorter. The second lab mainly deals with packing.
Questions
- Does the sample match any existing signatures on VT ?
- Are there indicators that the sample is packed or obfuscated ? If it is packed unpack it if possible.
- Do any imports hint at the program’s functionality ? Which Imports are there and what do they tell you ?
- What host and network based indicators could be used to identify this malware on infected machines ?
Unpacking
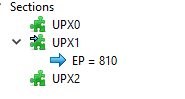
Running the file through Detect it easy and PE Bear we see that the sections have weired names like UPX1 and the signature suggests that this file is indeed packed with the upx packer.
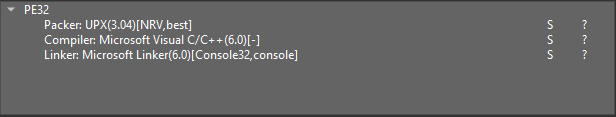
Luckily, it is really easy to unpack files packed with upx. All we need to do is to donwload the upx packer program and run the unpack command.
| |
Hashes
Packed
- MD5
8363436878404da0ae3e46991e355b83 - Sha1
5a016facbcb77e2009a01ea5c67b39af209c3fcb - SHA 256
c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a6
Unpacked
- MD5
ae4ca70697df5506bc610172cfc288e7 - SHA1
31e8a82e497058ff14049cf283b337ec51504819 - SHA256
8bcbe24949951d8aae6018b87b5ca799efe47aeb623e6e5d3665814c6d59aeae
Strings
Packed
| |
Unpacked
| |
Sandboxes
- [VT Report](VirusTotal - File - c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a6)
- Malware Bazaar
- Unpac Me
Imports from the unpacked sample
Kernel32.dll
| |
Advapi32.dll
| |
Wininet.dll
| |
Answers
- There are existing signatures for the packed as well as for the unpacked sample. Most of them label the sample as generic Win32 malware / Trojan
- The sections of the PE file being named
UPX0toUPX2hint at the fact that this sample is packed with upx. Luckily unpacking with UPX is as easy as calling the upx.exe with the right cli flags-d - The unpacked sample imports functions from
kernel32.dll,advapi32.dllandwininet.dll. Thekernel32.dllimports provide functionality for creating threads, creating and opening mutexes, exiting processes, retrieving filepaths for modules loaded by the current process, creating waitable timers and waiting for objects. Theadvapi32.dllimports functionality for creating a windows service, connecting a service to the ServiceControlDispatcher and opening the service control manager database. The last one requires administrator priviliges or it will fail. Thewininet.dllimports provide functionality to initialize usage of the wininet functions and to open a resource via a FTP or HTTP URL. This could mean that the sample will try to create tasks as threads which will be awaited. It might persist by trying to establish itself as a Windows Service which is run on startup. The Network capabilities imported viawininet.dllare a hint that the sample might try to download files or data from a C2 server. - A network-based indicator is the URL
http://www.malwareanalysisbook.comfound in the extracted strings from the unpacked sample. A host-based indicator might be the Windows Service started by the maleware. The unpacked strings contain the namesMalServiceandMalservicewhich could be the names used for the service created by the malware.