Practical Malware Analysis Chapter 1 Lab 1

After being interested in the topic of Malware Reversing/Research for a while now and picking Practical Malware Analysis last month. I started working through it this week and, as of now, really enjoying it. The first chapter concentrates on the basics of static analysis of binaries. As the author states himself, a lot of the specifics in the book are now out of date. For example, the Labs are originaly designed for Windows XP. I will be running my static analysis from a Windows 10 VM, as it shouldn’t make much of a difference for static. As soon as we get into dynamic analysis in Chapter 3 I will have a look into extending my virtual lab with a XP machine.
So, what are we doing ?
The book provides us with a collection of different Labs in the form of binary executable and library files. For each of these we are provided with a list of questions which should act as a guiding path through the analysis.
The first Lab actually provides us with 2 Files. An executable (.exe) file and a library file (.dll). Some of the tools suggested by the authori are still a good option, but 10 years after the book’s release there is a lot of new and shiney tools to choose from.
Tools
For the first Lab we will not require a lot of tools. I decided for the following for basic static analysis of the provided file.
Questions
- Upload the File to Virustotal. Check if there are existing Anti Virus signatures against this sample.
- When were the files compiled ?
- Is there any indication that any of these files is packed or obfuscated ? If so which are those indicators ?
- Do any imports hint at what this malware does ? If so, which imports are they ?
- Are there any other files or host-based indicators that you could look for on the infected systems ?
- What network-based indicators could be used to find this malware on infected machines ?
- What would you guess is the purpose of these files ?
Hashes
We use Detect it easy to collect basic information about the files. The first are hashes, which can be used for further reaseach.
Executable
- MD5
bb7425b82141a1c0f7d60e5106676bb1 - SHA1
9dce39ac1bd36d877fdb0025ee88fdaff0627cdb - SHA256
58898bd42c5bd3bf9b1389f0eee5b39cd59180e8370eb9ea838a0b327bd6fe47
DLL
- MD5
290934c61de9176ad682ffdd65f0a669 - SHA1
a4b35de71ca20fe776dc72d12fb2886736f43c22 - SHA256
f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba
Virustotal
To avoid uploading irrelevant files to virustotal I used the hashes to search for the files.
Executable
- Report
- 55/72 Vendors detect the file as malicious
- Imports:
- Kernel32.dll
- MSVCRT.dll (entrypoint)
- Sections:
- .text
- .rdata
- .data
- the sample gets mostly detected as a Win32 Trojan/Agent
- Malwarebytes flags the sample as a
Systemkiller - the sample contacted the following IPs according to VT:
| |
DLL
- the sample dll is detected by 45/71 vendors as malicious
- Imports:
- Kernel32.dll
- MSVCRT.dll (entrypoint)
- WS2_32.dll (network)
- sections:
- .text
- .rdata
- .data
- .reloc
- also mostly recognized as a trojan
Malware Bazaar
Another good source for information on malware is Malware Bazaar. It also gives access to an enormous collection of malware samples.
Executable
- Report
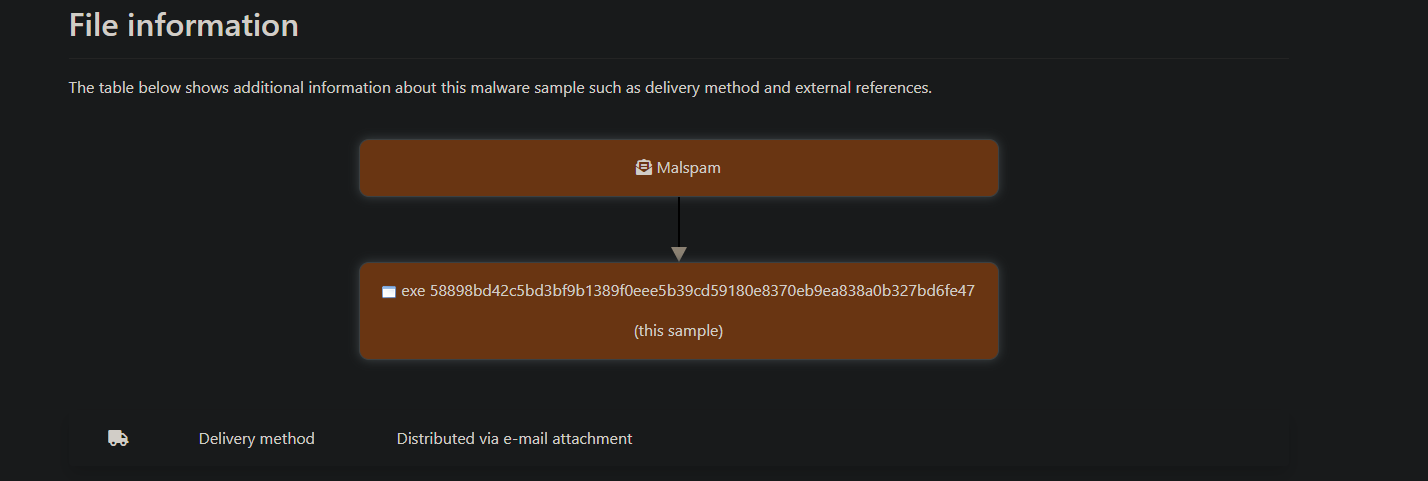
- malware bazaar gives file information which claim the file was delivered via Malspam
DLL
- there was no information for the dll hashes on malware bazaar
Unpac Me
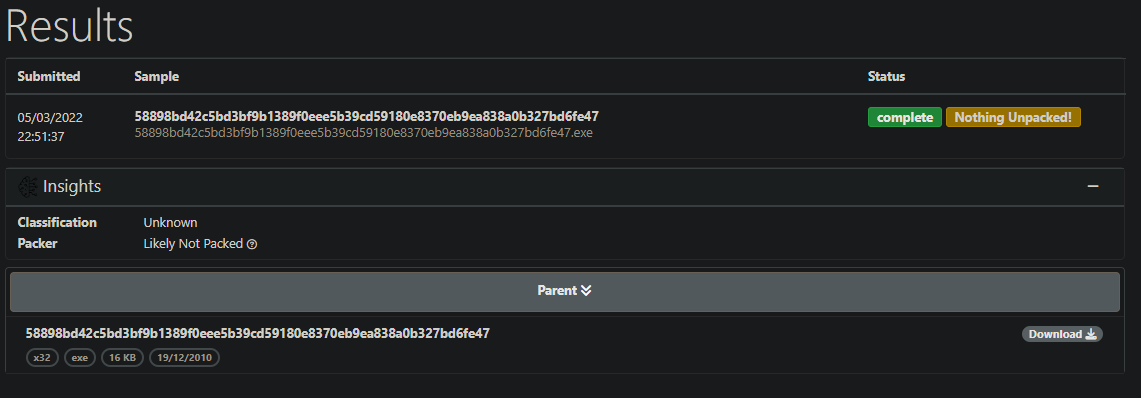
Event though Detect it easy tells us the files are not packed, if they were we could use unpac me to check if there are unpacked second stages for files with the same hashes as our executable or dll.
- Report
- as we see there is nothing to unpack
Strings
Executable
| String | Offset |
|---|---|
| CloseHandle | 0x2126 |
| CreateFileA | 0x217c |
| CopyFileA | 0x21b8 |
| FindFirstFileA | 0x21a6 |
| FindNextFileA | 0x2196 |
| KERNEL32.dll | 0x21c2 |
| malloc | 0x21d2 |
| MSVCRT.dll | 0x21e2 |
| kerne132.dll | 0x3010 |
| kernel32.dll | 0x3020 |
| C:\windows\system32\kerne132.dll | 0x304c |
| Kernel32. | 0x3070 |
| Lab01-01.dll | 0x307c |
| C:\Windows\System32\Kernel32.dll | 0x308c |
| WARNING_THIS_WILL_DESTROY_YOUR_MACHINE | 0x30b0 |
- we can see that the imported dlls we saw in the virustotal report show up in the extracted strings as well
- we also see that the sample contains strings which reference functions for File Creation with
CreateFileA, File Copying withCopyFileAas well as looking through a list of files withFindFirstFileAandFindNextFileA - we can also see a string referencing a dll contained in the same directory as the lab executable
Lab01-01.dll - the name
kern132.dllseems curious as it seems like a try at hiding the name by being so similiar tokernel32.dll - shortly after that we see a reference to the path
C:\windows\system32\kerne132.dll - this looks oddly similiar to the actual path to
kernel32.dllmentioned laterC:\Windows\System32\Kernel32.dll - as this sample seems to able to write and copy files we might assume that this sample injects the mention
Lab01-01.dllunder the fakekernel32.dllpath we saw - the last extracted string
WARNING_THIS_WILL_DESTROY_YOUR_MACHINEis also interesting - it might be the reason Malwarebytes flagged the sample as a
Systemkiller
DLL
| |
- as we can see there are some function names which seem to be imported by the dll
- we can also spot an IPv4 address looking string
127.26.152.13
Inspecting Imports
To get a further understanding of which functionality is provided by the files we will look at the imports from the Windows API.
We will use PE Bear to inspect the import tables for the executable and the dll.
Exectuable
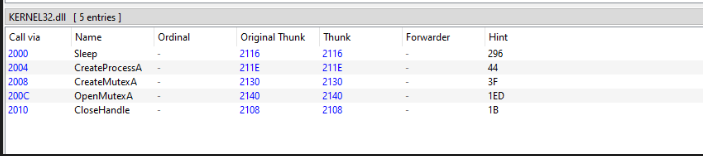
The executable imports a set of Functions from kernel32.dll.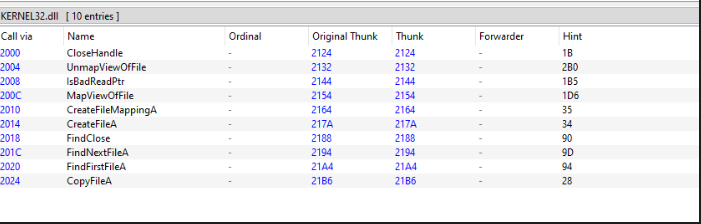
DLL
The dll imports functionality from 2 different dlls.
It imports functionality to create a Mutex, a data structure often used by malware to gurantee that only one instance of it runs on a system and it doesn’t re-infect it unnecessaryly.
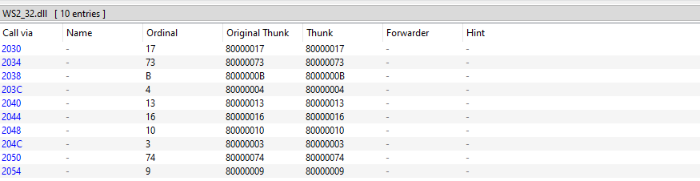
The other dll which functions are imported from is ws2_32.dll, a library used for network communication.
as we can see here the functions imported from ws2_32.dll are not imported by name but by ordinals
- ordinal numbers are identifiers for functions exported by a dll, when accessing exported functions these can either be referenced by their name or the ordinal number
- the problem with ordinal numbers used for imports is that these are not consistent across software versions
- this required me to do some research as the sample is over 10 years old at this point, so I will have to consult an older source for imformation about
ws2_32.dllordinal numbers - luckily i found this repository on github which is also about 10 years old, I will try to use this list to determine which functions are imported
- the code:
| |
- the list of ordinals in PE Bear is given as hexadecimal values (as there are values such as
B) - the script above extracts the name for each of them from the dictionary
- this resulted in the following list:
| |
- this looks like it would be the correct set of functions for communication with a C2
- the imports include:
- function to initialize usage of
ws2_32.dllwithWSAStartup - function to
connectto a remoteinet_addr - structs for a
socketand aninet_addr - function to receive data from a socket with
recv - function to send data over a socket with
send - function to parse bytes to be send from system bitness to TCP/IP bitness with
htons - function to close the socket with
closesocket - function to stop communication over a socket with
shutdown - function to end usage of
w2_32.dllwithWSACleanup
- function to initialize usage of
Answers
- There are alot of detections for the sample .exe as well as for .dll. As the samples are pretty old (> 10 years) there is a lot of different information that can be found on various Scanner Sites and Sandboxes. Some Information indicate that the executable was, at some point, delivered via a malspam campaign. Most signature hits determine the executable and the dll to be generice Win32 Malware / Trojans
- Detect it Easy shows Time Date Stamps of
2010-12-19 17:16:19for the .exe sample and2010-12-19 17:16:38for the .dll - Looking at the entropy of the files and online unpackers like unpac me they show no indicators that either of the files was packed or obfuscated
- The imports of the .exe file hint at the fact that its purpose is to write and copy file as well as jump through a list of files. The .dll file imports functions from kernel32.dll to create a process as well as a mutex (a lockable type ) and the sleep. It also imports some functions from
ws2_32.dllby their ordinal numbers. After a quick research it seems like the functions exported are the basic functionality used to communicate over the internet with a potential C2-Server. - A host-based indicator might be the .dll file coming with the executable
Lab01-01.dll - The extracted strings from
Lab01-01.dllcontain an IPv4 address127.26.152.13 - As stated above the provided samples
Lab01-01.exeandLab01-01.dllprovide the functionality to write and copy files to the system which hints at some kind of persistence via a file written to disc. Network capabilities and the IP address found might be an indicator that this sample establishes a connection to the C2 to receive further instructions. As the sample also is able to create a new process withCreateProcessAit might be able to receive shellcode from the C2 server which is then ran.